- The highlighted ransomware attacks resulted in substantial financial losses, reaching billions of dollars collectively.
- Attackers employed sophisticated tactics, such as exploiting software vulnerabilities and utilising social engineering techniques like phishing emails, to infiltrate systems and maximise their impact.
- Ransomware attacks targeted organisations across various industries globally, demonstrating the widespread nature of the threat.
Ransomware attacks represent a significant threat in today’s digital landscape, leaving devastating impacts on organisations worldwide. In this blog post, we will show the five most significant ransomware attacks in history, each showcasing the extent of financial losses, sophisticated strategies of the attackers, and the pressing need for robust cybersecurity measures.
1. ExPetr
Type of attack: Ransomware (a wiper exploiting an SMB vulnerability)
Year: 2017
Attackers: Likely Russian state-sponsored actors
Target company: Various, but severely impacted Maersk and Merck
Monetary impact: Estimated $10 billion
In June 2017, the ExPetr, also referred to as NotPetya, ransomware assault swept across the world, resulting in substantial disruptions and damages. Diverging from typical ransomware tactics, ExPetr wasn’t crafted to demand ransom money; rather, its aim was to inflict maximum harm. Initially targeting Ukraine, it proved too virulent to be confined.
NotPetya was soon identified as a wiper — a form of malware engineered to erase data — masquerading as ransomware. It exploited a vulnerability in Windows systems known as EternalBlue.
The wiper rapidly propagated, encrypting the master boot record (MBR) to render affected systems unbootable. Upon infiltrating a network, it employed various techniques, including the Mimikatz tool, to gather credentials and propagate laterally.
The collective financial toll attributed to NotPetya was estimated at approximately $10 billion, rendering it the most costly documented attack in history.
Also read: World’s largest bank hit by LockBit ransomware gang linked to Boeing, Ion attacks
2. WannaCry
Type of attack: Ransomware (vulnerability in SMB protocol)
Year: 2017
Attackers: Believed to be the Lazarus Group
Target company: Multiple (global attack); Microsoft Windows users
Monetary impact: Estimated $4 billion
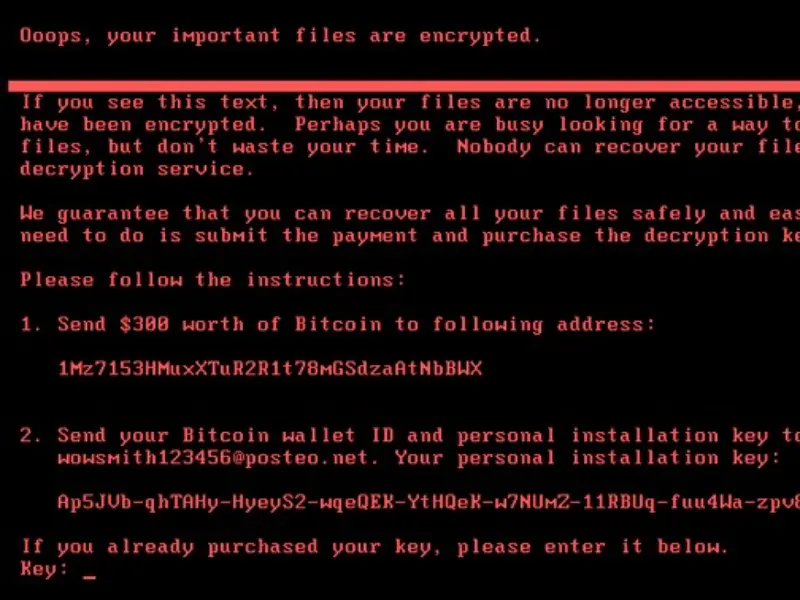
In May 2017, the WannaCry ransomware attack hit 150 countries, affecting over 200,000 computers. Initial cost estimates reached $4 billion, with potential future losses in the U.S. alone projected to exceed $7 trillion.
WannaCry exploited a critical vulnerability in Microsoft’s implementation of the Server Message Block (SMB) protocol known as EternalBlue, allegedly developed by the US National Security Agency (NSA) and leaked by the Shadow Brokers group.
The ransomware encrypted files on victims’ computers, demanding payment in Bitcoin for a decryption key, typically $300, doubling if not paid within three days. Acting as a worm, WannaCry spread automatically through networks, causing widespread disruption to critical infrastructures like healthcare, finance, and transportation.
Also read: EvilProxy Phishing Campaign Targets Microsoft 365 Users, Focuses on C-Level Executives
3. GandCrab
Type of attack: Ransomware-as-a-service (RaaS) (phishing, exploit kits)
Year: 2018-2019
Attackers: Unknown, operators announced ‘retirement’ in 2019
Target company: Various, including businesses and individuals (PCs using MS Windows)
Monetary Impact: Estimated over $2 billion
In 2018, GandCrab emerged as a highly pervasive and profitable ransomware attack. What distinguished GandCrab was its Ransomware-as-a-Service (RaaS) approach, wherein affiliates were licensed to carry out attacks and share profits with the developers.
GandCrab spread primarily through phishing emails and exploit kits, notably the GrandSoft and RIG kits. Upon infecting a victim’s system, GandCrab encrypted files and demanded a ransom in Dash cryptocurrency for decryption.
4. Locky
Type of attack: Ransomware (phishing emails distributing a macro in a Word document)
Year: 2016 – 2018
Attackers: Unknown, possibly the Dridex hackers (aka Evil Corp or TA505)
Target company: Various (predominantly healthcare providers in the US, Canada, France, Japan, Korea, and Thailand)
Monetary Impact: Estimated $1 billion
Locky, active mainly from 2016 to 2018, stood out as one of the most widespread ransomware variants, propagated through extensive phishing campaigns. It infiltrated systems via email attachments containing malicious Word documents. Upon opening the document and enabling macros, the ransomware payload was downloaded and activated.
Locky encrypted various types of data files, scrambled their filenames, and demanded payment in Bitcoin for decryption. Notably, it could encrypt files stored on network shares, increasing its potential for harm. Using a mix of RSA and AES encryption, Locky rendered victim files inaccessible until a ransom was paid, typically ranging from 0.5 to 1 Bitcoin.
Also read: HKBN offers free phishing assessments to SPO
5. Ryuk
Type of attack: Ransomware (usually TrickBot infection)
Year: 2018 – 2020
Attackers: Unclear, possibly various groups using the Ryuk malware or Wizard Spider (Russia)
Target company: Various, mostly healthcare and municipalities
Monetary Impact: Estimated $150 million
Debuting in mid-2018, Ryuk ransomware swiftly emerged as a significant menace to large-scale enterprises. Diverging from typical ransomware tactics reliant on automated distribution, Ryuk is manually deployed following an initial network breach. Attackers meticulously map networks, extract data, and gather credentials before unleashing Ryuk ransomware, aiming for maximal disruption.
Ryuk employs a blend of RSA-2048 and AES-256 encryption, rendering it highly resistant to decryption without the requisite keys. Moreover, the malware is engineered to encrypt network drives, resources, and remote hosts. Ryuk has been linked to numerous high-profile attacks, with ransom demands spanning from 15 to 500 Bitcoin (approximately $100,000 to $3.7 million).