- The internet’s infrastructure is a complex yet beautifully orchestrated system that enables seamless global communication and information exchange.
- Since its founding in 1969, the Internet has grown from four host systems to tens of millions.
- In fact, every device connected to the Internet is part of the network, even the devices in your home.
What comprises the basic underlying structure of the Internet? From name servers, to network access points, to backbone networks, the internet’s system of transferring data and information happens across what we call its infrastructure – the building blocks of the internet.
First, you need to know how your computer connects to other computers.
Computer network hierarchy
Every device connected to the Internet is part of the network, even the devices in your home. F or example, your computer may be connected to an Internet Service provider (ISP) using a cable or fiber optic modem. At work, your device may be part of a local area network (LAN), but your Internet connection is provided by your employer’s ISP. Once you connect your computer, it becomes part of your employer’s network. The ISP can then connect to a larger network. The Internet is just a network of networks.
Large communications companies have their own dedicated backbone, always-on Internet connections with enough bandwidth to allow many people to use the connection at the same time. In each region, the company has a local office that connects local homes and businesses to its main network. Surprisingly, there is no centralised network. Traffic is transmitted from one point to another, and if one computer drops out of the network, the packets that make up the digital file are routed to the other computer. Files arrive as expected, and you’ll never notice a change in traffic patterns.
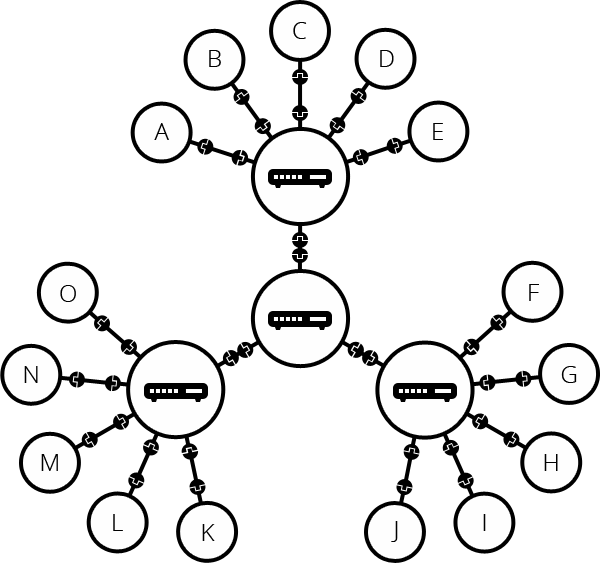
Here is an example of an Internet network:
Imagine that Company A is a small company with an office network set up with servers and networked printers. Suppose Company B is an enterprise ISP. Company B builds or leases office space in major cities to store its servers and routing equipment. Company B is so big that it runs its own fiber-optic lines between buildings so that they are all connected to each other.
In this arrangement, all customers of Company A can communicate with each other and all customers of Company B can communicate with each other, but the networks of the two companies are not linked. Both companies can communicate internally, but neither can communicate with the other. Therefore, both Company A and Company B agree to connect to the Internet access point or IXP in each city. The two companies’ networks can now connect to each other using the Internet, as well as to other organisations.
This example shows how two companies’ networks communicate with each other, but the two companies are just a close-up example of how their two networks join the vast Internet. For a bird’s eye view of what these interconnected networks might look like, take a look at Barrett Lyon’s Opte project, which works to create an ever-evolving map of the Internet’s plumbing.
Function of internet routers
All of these networks rely on IXP, backbone networks, and routers to communicate with each other. The incredible thing about this process is that a message can leave one computer, travel halfway around the world through several different networks, and reach another computer in a fraction of a second!
The router determines where information is sent from one computer to another. Routers are dedicated devices that send messages from you and other Internet users that speed up along thousands of paths to their destinations. Routers have two separate but related jobs:
1. It ensures that information does not go where it is not needed. This is essential to prevent massive amounts of data from clogging up the connections of “innocent bystanders.”
2. It ensures that information reaches its intended destination.
In performing these two jobs, a router is very useful when dealing with two separate computer networks. It connects two networks, passing information from one network to the other. It also protects network interactions, preventing traffic on one network from unnecessarily spilling over to another. No matter how many networks are connected, the basic operation and functionality of the router remains the same. Since the Internet is a vast network of countless smaller networks, it is necessary for it to use routers.
Internet backbone
The National Science Foundation (NSF) created the first high-speed backbone network in 1986. Called NSFNET, it is a T1 line that connects 170 smaller networks together and runs at 1.5 Mbps (million bits per second). IBM, MCI and Merit worked with NSF to create the backbone, and the following year developed the T3 (45 Mbps) backbone.
The backbone is the Internet connection that allows a lot more traffic than the connection from your home to the central office around the corner. In the early days of the Internet, only the largest telecommunications companies had the ability to handle this bandwidth.
Today, more and more companies operate their own high-capacity backbone networks, all of which are interconnected on a variety of IXPs around the world. In this way, everyone on the Internet, no matter where they are or what provider they use, can talk to everyone else on the planet. The whole Internet is a huge, massive protocol for free communication between people.
Internet protocol: IP address
Every machine on the Internet has a unique identification number called an IP address. IP stands for Internet Protocol, which is one of two protocols that computers use to communicate over the Internet. The other is Transmission Control protocol, and the two are often referred to as one in the phrase TCP/IP. A protocol is a predefined way for people who want to use a service to connect to that service. “Someone” can be a person, but more often it is a computer program, such as a web browser.
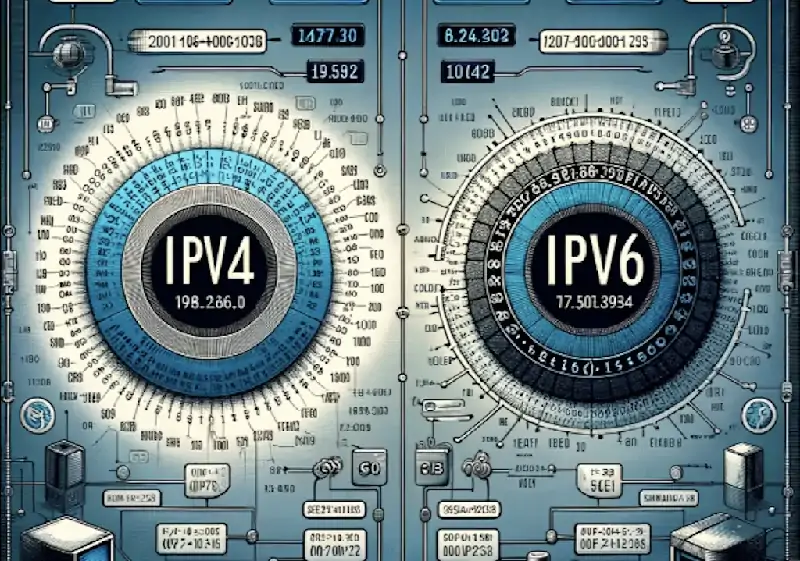
A typical IP version 4 (IPv4) address looks like this: 216.27.61.137.
For the convenience of our human memory, IP addresses are usually represented in decimal format as dot decimal numbers, as shown in the figure above. But computers communicate in binary form. View the binary file the same IPv4 address: 11011000.00011011.00111101.10001001.
Each sequence of numbers in an IPv4 address is called an octet because each sequence of numbers has eight positions when viewed in binary form. If you add all the positions, you get 32, because IPv4 addresses are treated as 32-bit numbers. Since each of the eight locations can have two different states (1 or 0), the total number of possible combinations for each octet is 28 or 256. Thus, each octet can contain any value between 0 and 255. Combine four octets together and you get 232 or possibly 4,294,967,296 unique values!
Of the nearly 4.3 billion possible combinations in IPv4 addresses, certain values are restricted to use as typical IP addresses. For example, IP address 0.0.0.0.0 is reserved for computers on the local network, and address 255.255.255.255 is used for broadcasting.
Although 4.3 billion addresses sounds like a lot, the Internet is growing so fast that an updated 128-bit address system is needed to replace IPv4. In late 1998, experts from the Internet Engineering Task Force (IETF) began developing a new system. IP Version 6 (IPv6), officially launched on June 6, 2012, has 340 trillion space-3 addresses, so we should leave plenty of room for all devices. (For now. For the record, IPv5 was never formally adopted as a standard.
As you might expect, IPv6 addresses look slightly different than IPv4, which was created in the 1970s. Each segment in an IPv6 address uses four numbers, separated by colons.
The example is as follows: ba5a: 9a72:4aa5:522e: b893:78dd: a6c4: f033.
Because IPv6 uses hexadecimal notation, 16 separate numbers need to be represented. So, in addition to the numbers 0 through 9, the letters A-F were also drafted to represent two digits.
Currently stuck with IPv4, the purpose of the octet is not simply to separate numbers. They are used to create classes of IP addresses that can be assigned to specific businesses, governments, or other entities based on size and need. The octet is divided into two parts: network and host. The first octet identifies the network to which the computer belongs. A host (sometimes called a node) identifies the actual computer on the network. The last octet shows the host segment. There are five IP classes and some special addresses.
When the Internet was in its infancy, it consisted of a small number of computers connected to modems and phone lines. You can only establish a connection by providing the IP address of the computer with which you want to establish a link. For example, a typical IP address might be 216.27.22.162. This was fine when there were only a few hosts, but as more systems came online, it became unwieldy.
The first solution to this problem is a simple text file maintained by the Network Information Centre (NIC) called the host table, which maps names to IP addresses. Soon, this text file became so large that it became too cumbersome to manage. In November 1983, Paul Mokapetris submitted two requests for comments to the International Network Working Group. RFC 882 Outlines the concept of the Domain Name System (DNS), which automatically maps text names to IP addresses. RFC 883 proposes a method for implementing this system. Thanks to his efforts and those of many others, this way you just have to remember www.howstuffworks.com, for example, instead of a series of numbers and punctuation marks for the IP address of HowStuffWorks.com.
Also read: How can I protect my IP address like a pro?
URL: Uniform Resource Locator
When you use the Web or send an email, you can use a domain name to do this. For example, uniform resource locator (URL) “https://www.howstuffworks.com” includes the domain name howstuffworks.com. So does this E-mail address: example@howstuffworks.com. Each time a domain name is used, the Internet’s DNS servers convert a human-readable domain name into a machine-readable IP address. See how name servers work to learn more about DNS.
Top-level domains, also known as level-1 domains, include.com,.org,.net,.edu, and.gov. Within each top-level domain, there is a huge list of second-level domains. For example, in the.com level domain, there are:
HowStuffWorks
Yahoo
Microsoft
Each name in the.com top-level domain must be unique. The leftmost part (such as “www”) is the host name. It specifies the directory name on a specific computer with a specific IP address in the domain. A given domain may contain millions of host names, as long as they are all unique within the domain.
DNS servers accept requests from programs and other name servers to translate domain names into IP addresses. When a request comes in, the DNS server can do one of four things:
1. It can answer the request with an IP address because it already knows the IP address of the requested domain.
2. It can contact another DNS server and try to find the IP address of the requested name. It may have to do this several times.
3. It can say, “I don’t know the IP address of the domain you’re requesting, but this is the IP address of a DNS server that I know better than I do.”
4. It may return an error message because the requested domain name is invalid or does not exist.
DNS
Suppose you type the URL www.howstuffworks.com in your browser. The browser contacts the DNS server to obtain the IP address. The DNS server starts the search for an IP address by contacting one of the DNS root servers. The root server knows the IP addresses of all DNS servers that handle top-level domains (.com,.net,.org, etc.). Your DNS server asks Root for www.howstuffworks.com, and Root says, “I don’t know the IP address of www.howstuffworks.com, but this is. COM IP address of the DNS server.
Then, your name server goes to. The COM DNS server sends a query asking if it knows the IP address of www.howstuffworks.com. The DNS server of the.com domain knows the IP addresses of the name servers that handle the www.howstuffworks.com domain, so it returns those addresses.
Your name server will then contact the DNS server to get www.howstuffworks.com and ask if it knows the IP address of www.howstuffworks.com. It does, so it returns the IP address to your DNS server, which returns it to the browser, which then contacts the server for www.howstuffworks.com to get the web page.
One of the keys to making this work is redundancy. There are multiple DNS servers at each level, so if one server fails, there are others to handle the request. Another key is caching. After resolving the request, the DNS server caches the received IP address. Once it issues any to the root DNS server. COM domain request, it will know to handle. The IP address of the DNS server of the COM domain, so it does not have to ask the root DNS server for that information again. The DNS server can do this for every request, and this cache helps keep things from getting bogged down.
Although they are completely invisible, DNS servers handle billions of requests every day, and they are essential to the smooth functioning of the Internet. The fact that this distributed database runs so well and invisibly works day in and day out is a testament to design.
Internet servers and clients
Every machine on the Internet is either a server or a client. A computer that provides services to other computers is a server. The computer used to connect to these services is the client. There are web servers, email servers, FTP servers, etc., to meet the needs of Internet users around the world.
When you connect to www.howstuffworks.com to read a page, you are a user sitting on a client computer. You are accessing the HowStuffWorks Web server. The server computer will find the page you requested and send it to you. The client accessing the server computer has a specific intent, so the client directs its requests to a specific software server running on the server computer. For example, if you run a Web browser on your computer, it will try to communicate with the Web server on the server computer instead of the email server.
The server has a static IP address that does not change. On the other hand, a home computer dialled through a modem usually has an IP address assigned by the ISP for each login. This IP address is unique to your session and may be different the next time you dial in. This way, the ISP only needs one IP address per device, rather than one IP address per customer.
Ports and HTTP
Any server provides its services using a numbered port, that is, a port for each service available on the server. For example, if the server computer is running a Web server and a File Transfer Protocol (FTP) server, the Web server is usually available on port 80 and the FTP server is available on port 21. The client connects to the service with a specific IP address and a specific port number.
Once a client connects to a service on a specific port, it accesses that service using a specific protocol. The protocol simply describes how the client and server will talk to each other. Every Web server on the Internet conforms to the Hypertext Transfer Protocol (HTTP). You can learn more about Internet servers, ports, and protocols by reading how Web servers work.
Also read: What purposes does encryption serve on internet servers?
Networks, routers, Naps, ISPs, DNS, and powerful servers all make the Internet possible. When you realise that all this information is being sent around the world in milliseconds, these components are extremely important in modern life – without them, there would be no Internet. Without the Internet, many of our lives would be very different.