- Cybersecurity compliance refers to adhering to standards and statutory requisites set by entities, laws or governing bodies. Companies handling digital assets need to implement controls and security practices to minimise the risk to sensitive data.
- Numerous compliance frameworks and standards exist to guide organisations in establishing robust cybersecurity practices, including the NIST Cybersecurity Framework, GDPR, HIPAA and PCI DSS.
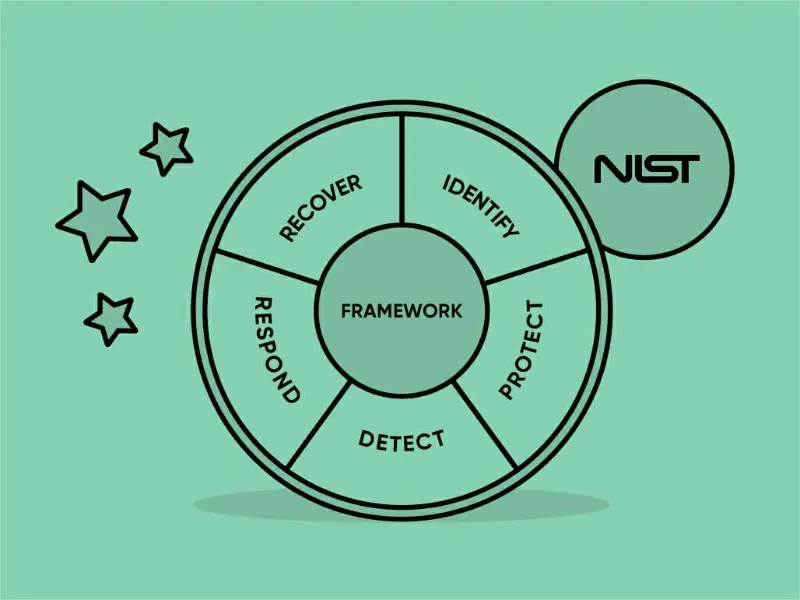
- The NIST Cybersecurity Framework is a set of guidelines for mitigating an organisation’s cybersecurity risks, published by the National Institute of Standards and Technology, the main components of which are “Core”, “Profile” and “Tiers”.
The exponential rise in cybercrime makes governments, businesses, and organisations focus on compliance and compliance regulations. The NIST Cybersecurity Framework is one of the widely recognised frameworks, the main components of which are “Core”, “Profile” and “Tiers”.
Cybersecurity compliance
Cybersecurity compliance refers to adhering to standards and statutory requisites set by entities, laws or governing bodies. Companies handling digital assets need to implement controls and security practices to minimise the risk to sensitive data.
The exponential rise in cybercrime often leads to massive data breaches or business disruptions. This has become among the primary drivers for this renewed focus on compliance and compliance regulations.
Numerous compliance frameworks and standards exist to guide organisations in establishing robust cybersecurity practices. These frameworks provide a structured approach to implementing security controls and addressing specific compliance requirements.
Some widely recognised frameworks include the NIST Cybersecurity Framework, the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA) and the Payment Card Industry Data Security Standard (PCI DSS).
Also read: How can generative AI be used in cybersecurity?
The NIST cybersecurity framework
The NIST Cybersecurity Framework is a set of guidelines for mitigating an organisation’s cybersecurity risks, published by the National Institute of Standards and Technology (NIST) based on existing standards, guidelines, and practices.
Also read: How to enhance cybersecurity after the Australian State Court database breach?
The framework, which “provides a high-level taxonomy of cybersecurity outcomes and methods for evaluating and managing those outcomes,” has been translated into multiple languages and is widely used by governments, businesses, and organisations, in addition to guidance on protecting privacy and civil liberties in the context of cybersecurity.
Version 1.0 of the framework was released in 2014 and was initially targeted at critical infrastructure operators. In 2017, draft version 1.1 of the framework was released for public comment and officially released to the public on April 16, 2018. The framework is divided into three parts: “Core”, “Profile” and “Tiers”.
1. Framework core
“Framework Core” contains an array of activities, outcomes and references about aspects and approaches to cybersecurity. The NIST Cybersecurity Framework organises its “core” material into 5 “functions”, identify, protect, detect, respond and recover.
These functions are subdivided into a total of 23 “categories”. For each category, it defines several subcategories of cybersecurity outcomes and security controls, with 108 subcategories in all.
2. Framework profile
A “Framework Profile” is a list of outcomes that an organisation has chosen from the categories and subcategories, based on its needs and risk assessments.
An organisation typically starts by using the framework to develop a “Current Profile” which describes its cybersecurity activities and what outcomes it is achieving. It can then develop a “Target Profile”, or adopt a baseline profile tailored to its sector (e.g. infrastructure industry) or type of organisation, which defines steps for switching from its current profile to its target profile.
3. Framework implementation tiers
Organisations use the “Framework Implementation layer” to clarify to themselves and their partners how they view cybersecurity risks and the complexity of their approach to managing them. Tiers reflect an increasing degree of expertise in cyber risk management practices.
Tier 1 Partial includes companies with on-demand or no security procedures.
The majority of corporate executives in Tier 2 Risk-informed are now aware of the main threats they face, including malware, state-sponsored attacks, and other bad actors.
Tier 3 Repeatable is for companies with risk management and cybersecurity best practices that have received executive approval.
Tier 4 Adaptive is the topmost tier and requires the greatest time and money to deploy, but it is essential in heavily regulated industries like banking, healthcare, and critical infrastructure.