- A network port is a logical connection point that directs incoming and outgoing data to specific applications or services on a device.
- Network ports play a vital role in cybersecurity, ensuring that only authorized traffic is allowed while blocking unauthorized attempts to exploit open ports.
A network port is an essential component in modern computing, acting as a logical access point for data traffic to enter and leave a device. With the increasing complexity of networks and the rise in cybersecurity threats, understanding how ports work and how to secure them is crucial for maintaining a safe and efficient network environment. In this article, we’ll dive deep into the role of network ports, their types, common use cases, and how to secure them effectively.
- What is a network port?
- Types of network ports
- Common use cases for network ports
- How network ports impact cybersecurity
- Best practices for port security
- Common issues with network ports
- The role of ports in efficient networking
- Physical ports vs. Virtual ports
- Securing network ports against cyberattacks
- Why network ports matter

What is a network port?
A network port is essentially a virtual entry point in a network that directs incoming and outgoing data traffic to specific applications or services on a device. Think of it like a door or window on a computer where data enters or exits based on the specific application or service that requires it. Ports are crucial in managing how data flows, ensuring that information reaches the right destination.
Each port is associated with a unique number, known as the “port number“, ranging from 0 to 65535. This system allows different services to run on a single device without conflict, as each service can be assigned its own port number. For example, HTTP traffic uses port 80, while HTTPS uses port 443. Without these virtual checkpoints, network devices would struggle to organize and manage multiple services running simultaneously.
Also read: What is a port and how do network ports affect cybersecurity?
Also read: The importance of network segmentation in cybersecurity
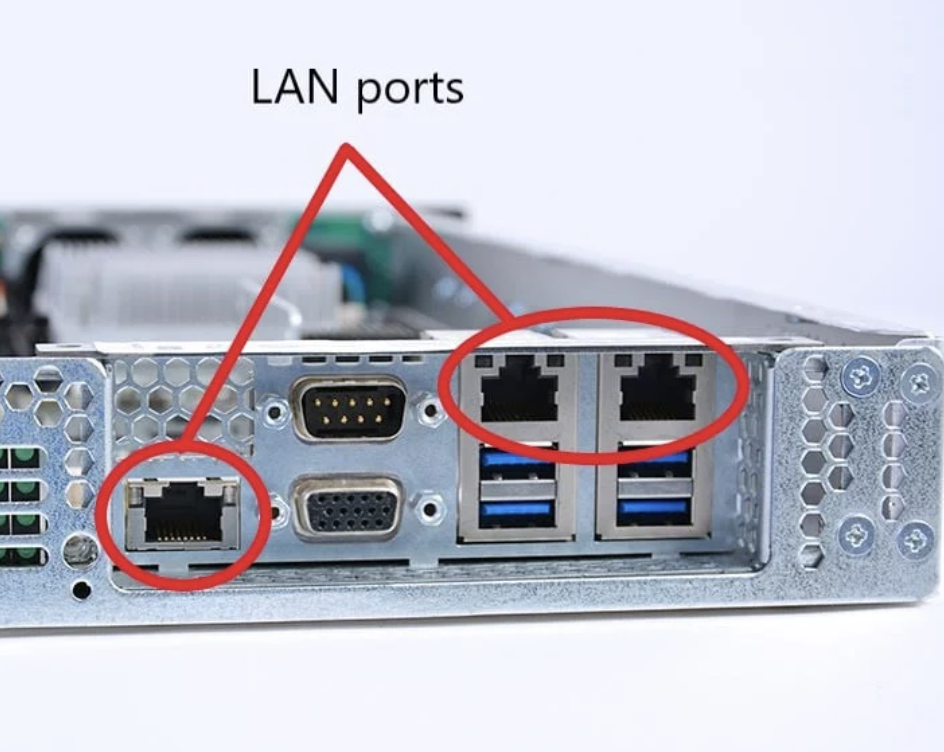
Types of network ports
Network ports are classified into several categories based on their function and scope of usage. Understanding the differences between these categories helps in managing network traffic effectively and securely.
- Well-Known Ports (0-1023): These ports are reserved for widely-used, standard services. For example, HTTP uses port 80, and SSH (Secure Shell) uses port 22. These ports are most often used for essential web-based applications, and they are strictly regulated to avoid conflicts.
- Registered Ports (1024-49151): These ports are used by applications and services that are not part of the core protocols but are still necessary for network communication. For instance, Microsoft SQL Server uses port 1433, and many enterprise-level applications use registered ports to function.
- Dynamic or Private Ports (49152-65535): These ports are used temporarily for ephemeral connections, meaning they are assigned dynamically when a connection is established. Once the session is over, the port is closed and can be reused by another application.
These categories allow a streamlined way of managing network services and reducing the risk of port conflicts.
Common use cases for network ports
Network ports serve a variety of purposes, each of which is vital for ensuring smooth communication between devices and services. Below are some of the most common use cases:
- Web Traffic (HTTP/HTTPS): Ports 80 and 443 are used for web browsing. HTTP traffic (port 80) is unencrypted, while HTTPS (port 443) ensures secure communication by encrypting the data.
- Email Communication (SMTP/POP3/IMAP): Email services rely on specific ports. For instance, SMTP (Simple Mail Transfer Protocol) uses port 25 for sending emails, while POP3 (Post Office Protocol 3) uses port 110 for receiving emails. IMAP (Internet Message Access Protocol) commonly uses port 143 for retrieving and managing messages.
- File Transfer (FTP/SFTP): FTP (File Transfer Protocol) uses port 21 to transfer files between servers, while SFTP (Secure FTP) uses port 22 to ensure secure data exchange over the network.
Ports help ensure that each service is neatly separated from the others, allowing multiple applications to function simultaneously on the same device.
Also read: What is classification in neural networks and why is it important?

Cybersecurity is not just a necessity; it is the cornerstone of digital trust.
Satya Nadella, CEO of Microsoft
How network ports impact cybersecurity
Network ports play a vital role in the overall security of a network. Open ports can serve as entry points for malicious activities such as cyberattacks and unauthorized access attempts. Hackers often use techniques like port scanning to detect open ports and identify vulnerabilities.
In a well-managed network, firewalls help protect ports by allowing only traffic that is necessary for specific services. For example, if an employee is trying to access a service on a port not assigned to that service, the firewall will block the connection. Similarly, if an attacker tries to exploit an open port, such as the well-known RDP port 3389 for Remote Desktop Protocol, firewalls can block the connection and prevent a breach.
Proper port management helps reduce the attack surface, making it much harder for attackers to exploit vulnerabilities. As part of an overall cybersecurity strategy, it’s essential to regularly monitor and secure network ports.‘
Also read: What is network monitoring and why is it important?
Also read: The importance of network segmentation in cybersecurity

Best practices for port security
Securing network ports is crucial for maintaining a robust cybersecurity posture. Implementing effective port security strategies helps protect devices and services from unauthorized access. Below are some best practices for securing network ports:
- Close Unused Ports: Keeping only necessary ports open is one of the easiest ways to improve network security. Any unused port should be closed to prevent potential access points for cybercriminals.
- Use Firewalls: Firewalls should be configured to allow only the required ports for essential services while blocking access to others. For instance, if a company is running a web server, they may configure their firewall to only allow HTTP traffic on port 80 and HTTPS on port 443.
- Regular Port Scanning: Regularly scanning ports allows network administrators to identify potential vulnerabilities and mitigate threats before they can be exploited.
- Port Filtering: Advanced network security tools can filter traffic based on specific port numbers and prevent any unwanted access to critical ports.
By following these best practices, organizations can significantly reduce the risk of security breaches and unauthorized access.
Also read: What is network firewall protection and why is it important?
Common issues with network ports
Network ports, while essential for efficient communication, can sometimes fail, leading to network connectivity issues. Here are some of the most common problems associated with network ports:
- Power Surges: Power surges, which often occur due to electrical faults, can cause physical damage to ports, rendering them inoperable.
- Water Damage: Exposure to moisture or water can lead to malfunctions in the hardware components of the port, disrupting the device’s connectivity.
- Hardware Failures: Internal issues such as component breakdowns can cause the ports to stop functioning, even if the device appears to be working normally.
- Cable Pin Damage: Inserting cables forcefully or using them improperly can damage the pins inside the ports, leading to connection failures.
When dealing with a faulty port, it’s important to investigate both hardware and software issues that may be contributing to the problem. Often, ports will operate independently, meaning that if one port fails, other ports on the device may still work.

The role of ports in efficient networking
Ports are essential for ensuring that networked devices communicate effectively without interference. They allow multiple applications and services to run simultaneously without causing traffic bottlenecks. By assigning a unique port number to each service or application, network devices can direct traffic to the right destination with high efficiency.
In addition, ports make it easier to monitor and control data flow. Network administrators can prioritise traffic based on the application or service it’s destined for, ensuring that critical services get the resources they need without delay. For example, a server may prioritize web traffic over email traffic to ensure that websites load quickly for users.

Physical ports vs. Virtual ports
While virtual ports manage data flow on a logical level, physical ports on devices (such as USB or Ethernet ports) are the tangible connectors that facilitate the physical connection between devices. For example, a computer may have multiple Ethernet ports for wired network connections or USB ports for connecting peripherals like keyboards and mice.
The key difference between physical and virtual ports is that physical ports allow for direct, physical connections, while virtual ports are used for managing data and applications within a network environment. Both types of ports are necessary for the smooth functioning of modern computing systems.

Securing network ports against cyberattacks
As cyber threats evolve, network ports become prime targets for attackers looking for ways to exploit vulnerabilities. Securing ports involves proactive monitoring, blocking unused ports, and using tools like intrusion detection systems (IDS) to identify and respond to threats in real time.
When a network device has multiple open ports, it provides more opportunities for attackers to exploit weaknesses. Using firewalls and ensuring that only necessary ports are open significantly reduces the chances of a successful attack. Regular port scans can also help identify vulnerabilities that might otherwise go unnoticed.
Also read: How does Axiado’s chip prevent cyberattacks?
Also read: Pro-Russian hacker groups are launching cyberattacks on S Korea
In the world of networking, even a tiny port can open up a universe of vulnerabilities—or opportunities.
Anonymous Tech Innovator
Why network ports matter
Network ports are vital to the functioning of computer networks, facilitating communication between devices and services. However, if not properly managed and secured, ports can be a significant security risk. By understanding how ports work and how to secure them, businesses and individuals can maintain efficient, secure networks that are resistant to cyberattacks.
Also read: RTP network raises transaction limit to $10M to support business growth
Also read: The importance of network segmentation in cybersecurity
Well-known ports (0-1023) are reserved for standard services like HTTP (port 80) and HTTPS (port 443). Dynamic ports (49152-65535) are temporary, assigned to applications for specific sessions, and released after use.
You can use tools like Nmap for comprehensive scanning or Netstat to view active connections and open ports. Firewalls and their logs can also provide insights into port activity.
Unsecured open ports are entry points for cyberattacks. Attackers may exploit them for data theft, malware installation, or denial-of-service attacks. Closing or securing unused ports reduces risks.
Firewalls monitor and control traffic, allowing only authorised connections to specified ports. They block unsolicited traffic and can detect unusual activity, safeguarding against potential threats.
Closing unused ports eliminates vulnerabilities, reduces attack opportunities, and enhances network performance by minimising unnecessary monitoring. Regular audits help maintain a secure configuration.

